Metasploit - Discovery Scans
Metasploit - Discovery Scans
The first phase of penetration involves scanning a network or a host to gather information and create an overview of the target machine.
Discovery Scan is basically creating an IP list in the target network, discovering services running on the machines. To do this in Metasploit, we will use the command promp which are NMAP commands incorporated in Metasploit. For more information on NMAP and its commands, go to https://nmap.org/
Now let’s see in practice how it exactly works. We started the target machine (Metasploitable) and the Windows Server 2003 machine with the IP 192.168.1.101.
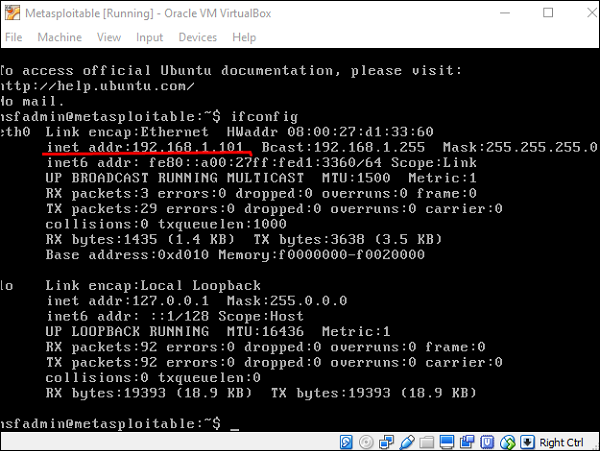
Next, we will start Metasploit. Here, we are using Kali Linux. Hence, the commands will always start with nmap.
Let’s start to scan the network with range 192.168.0.0/24 and discover the machines.
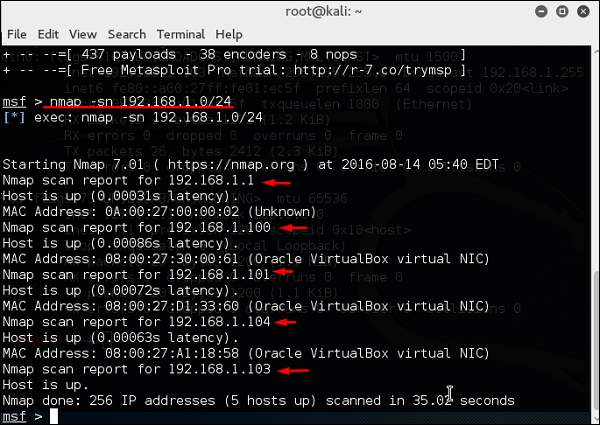
As can be seen in the above screenshot, there are 5 hosts up in the network with details. Now that we found the hosts that are alive, we will try to find the OS they are running on and their background services.
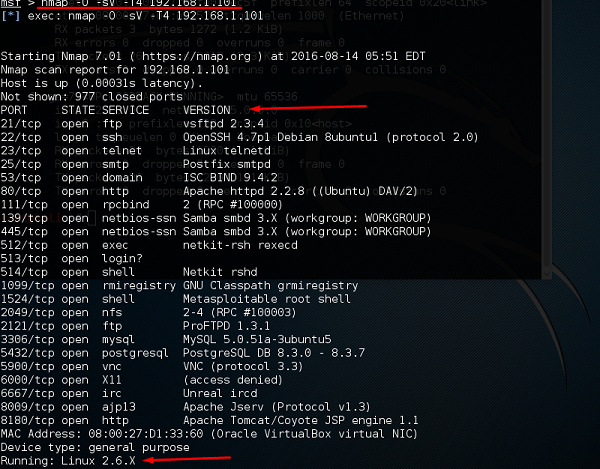
We will try to attack the vulnerable machine with the IP 192.168.1.101. To do so, we will run the following command −
Nmap –sV-O –T4 192.168.1.101Here,
- –sV parameter will detect the services with their version details.
- –O is to detect the version of OS which in our case is Linux 2.6.X
- –T4 is the time that we let the scan to finish
You will get the following screen as an output of using the above command.


Post a Comment