Metasploit - Social Engineering
Metasploit - Social Engineering
Social engineering can be broadly defined as a process of extracting sensitive information (such as usernames and passwords) by trick. Hackers sometimes use fake websites and phishing attacks for this purpose. Let us try to understand the concept of Social Engineering attacks through some examples.
Example 1
You must have noticed old company documents being thrown into dustbins as garbage. These documents might contain sensitive information such as Names, Phone Numbers, Account Numbers, Social Security Numbers, Addresses, etc. Many companies still use carbon paper in their fax machines and once the roll is over, its carbon goes into dustbin which may have traces of sensitive data. Although it sounds improbable, but attackers can easily retrieve information from the company dumpsters by pilfering through the garbage.
Example 2
An attacker may befriend a company personnel and establish good relationship with him over a period of time. This relationship can be established online through social networks, chatting rooms, or offline at a coffee table, in a playground, or through any other means. The attacker takes the office personnel in confidence and finally digs out the required sensitive information without giving a clue.
Example 3
A social engineer may pretend to be an employee or a valid user or an VIP by faking an identification card or simply by convincing employees of his position in the company. Such an attacker can gain physical access to restricted areas, thus providing further opportunities for attacks.
Example 4
It happens in most of the cases that an attacker might be around you and can do shoulder surfing while you are typing sensitive information like user ID and password, account PIN, etc.
Social Engineering Attack in Metasploit
In this section, we will discuss how you can initiate a Social Engineering attack using Metasploit.
First of all, go to the Home page of Metasploit and click Phishing Campaign, as shown in the following screenshot.
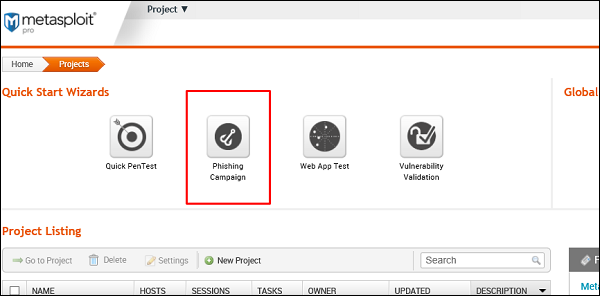
Enter the name of the project and click Next.
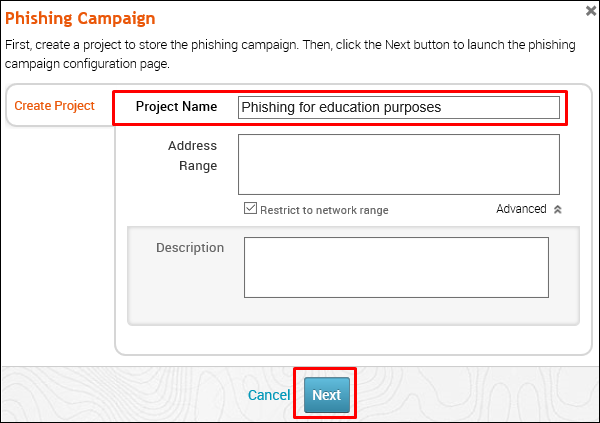
Enter the name of the campaign. In our case, it is Lab. Next, click the E-mailicon under Campaign Components.
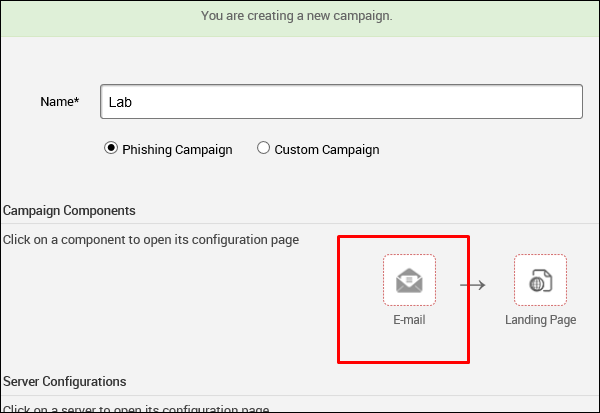
On the next screen, you need to supply the requested data according to your campaign.
Next, click the Content icon (number 2) if you want to change anything in the content of the email. After changing the content, click Save.
Next, click the Landing Page icon to set the URLs where you want to redirect your tricked users.
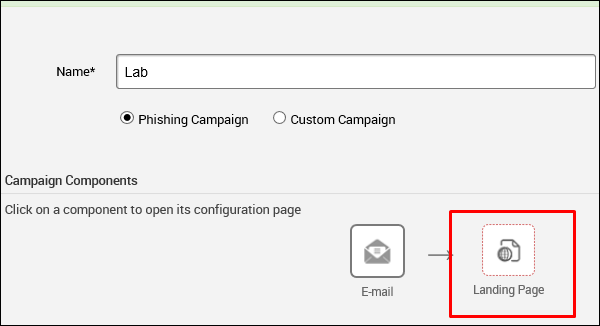
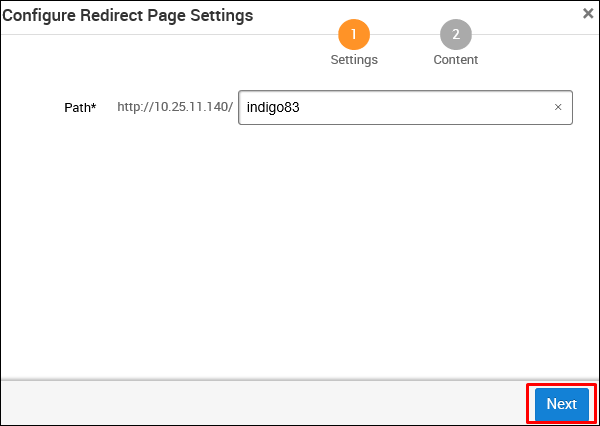
As shown in the following screenshot, enter the URL at Path and click Next.
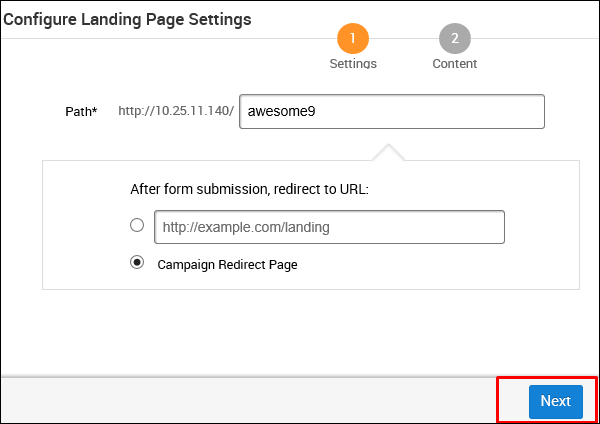
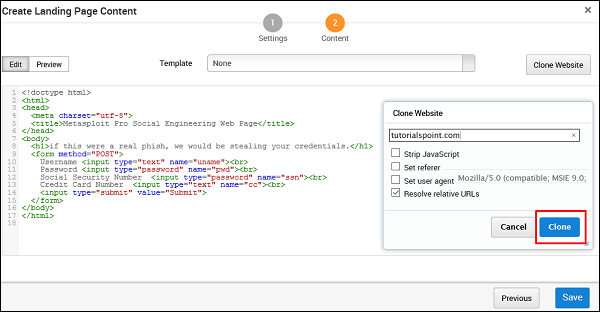
On the next screen, click the button Clone Website which will open another window. Here, you need to enter the website that you want to clone. As you can see in the following screenshot, we entered tutorialpoint.com in this field. Next, click the Clone button and save your changes.
Next, click the Redirect Page button.
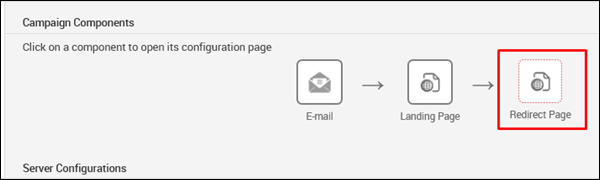
Click Next and you will get to see the following screen.
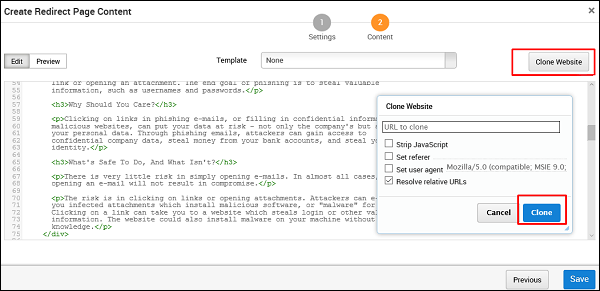
You can click the Clone Website button to clone the redirected website again.
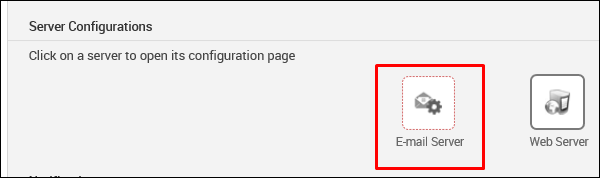
Next, in the Server Configuration section, click the E-mail Server button.
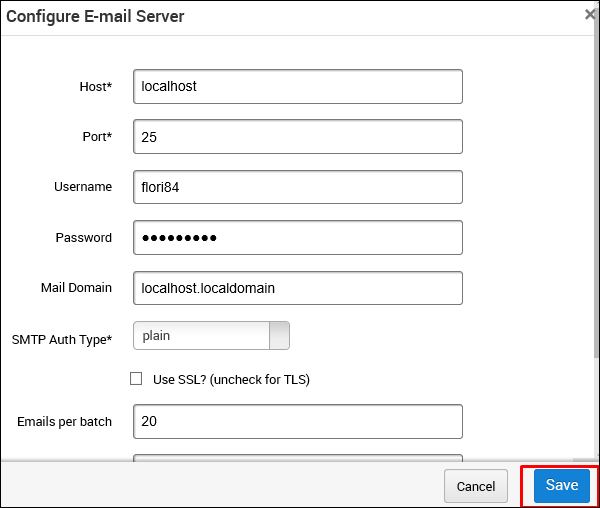
On the next screen, enter mailserver settings that will be used as a relay to send this phishing email. Then, click Save.
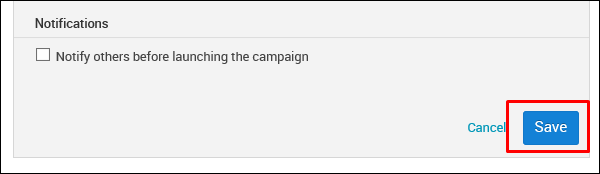
In the Notifications section, there is an option to Notify others before launching the campaign. You can choose to use this option to notify others. Then, click Save.
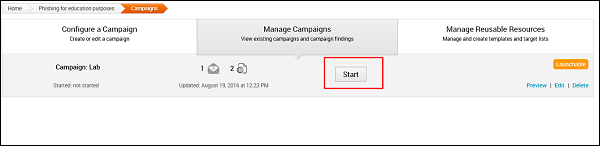
Next, you will see a new window. Here, you need to click the Start button to initiate the process of sending phishing mails.
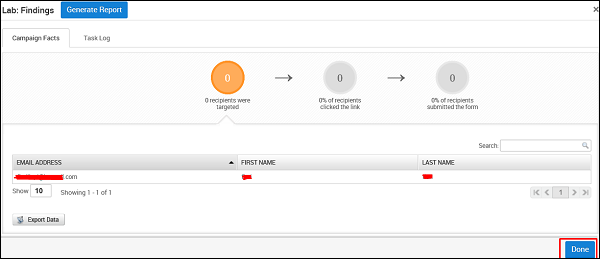
Metasploit has options to generate a statistical report of your phishing campaign. It will appear as shown in the following screenshot.


Post a Comment