Metasploit - MetaModules
Metasploit - MetaModules
MetaModules are complex and automated security tasks, designed to help security departments to do their job more efficiently, like testing firewall ports which are open and closed, testing default credentials, etc.
MetaModules are new features that are introduced in Metasploit Pro (the commercial version). You should keep in mind that the MetaModules with best rating of stars will you provide the best results.
To open MetaModules, go to Home → Project Name → Modules → MetaModules.
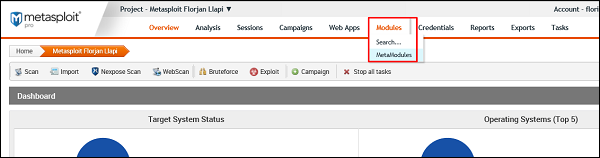
As you can see, we have six metamodules to serve different requirements.
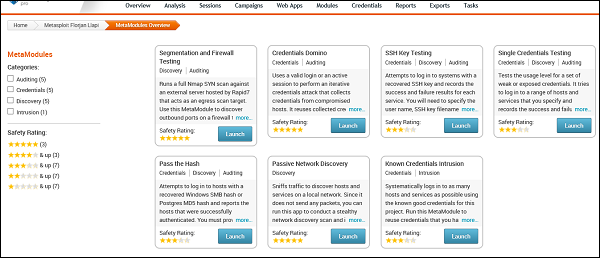
Segmentation and Firewall testing
This MetaModule runs a full Nmap SYN scan against an external server hosted by Rapid7 that acts as an egress scan target. Use this MetaModule to discover outbound ports on a firewall that an attacker can use to filter information. You will need to specify the ports and protocols that you want to audit.
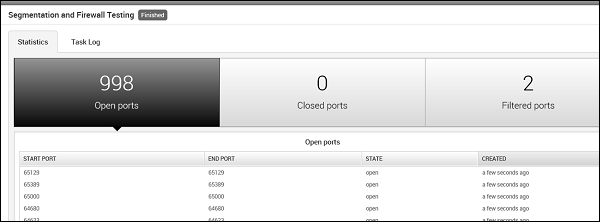
To run this MetaModule, click the Launch button and follow the instructions in there. It will show you a report of open, closed, and filtered ports, just as shown in the following screenshot.
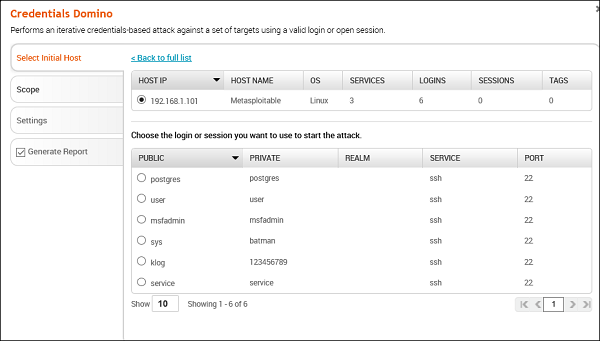
Credentials Domino
This MetaModule uses a valid login or an active session to perform an iterative credentials attack that collects credentials from compromised hosts. It reuses collected credentials to identify other possible attack routes. This MetaModule runs until it tries all credentials or reaches a termination condition.
To run this MetaModule, click the Launch button on the opening screen. It will produce the following screenshot wherein you have to choose the HOST IP and the Login credentials to be tested.
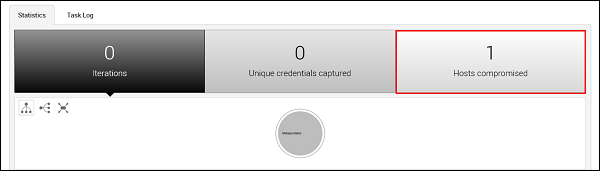
If the credentials that you have entered is correct, then it will produce the following result.
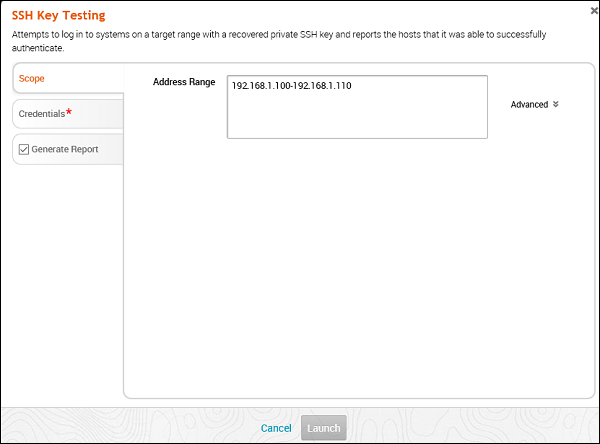
SSH Key Testing
This MetaModule attempts to log in to systems with a recovered SSH key. It records the success and failure results for each service. You will need to specify the user name, the SSH key filename, and the range of hosts that you want.
To run this MetaModule, click Launch on the opening screen. It will display the following screen.
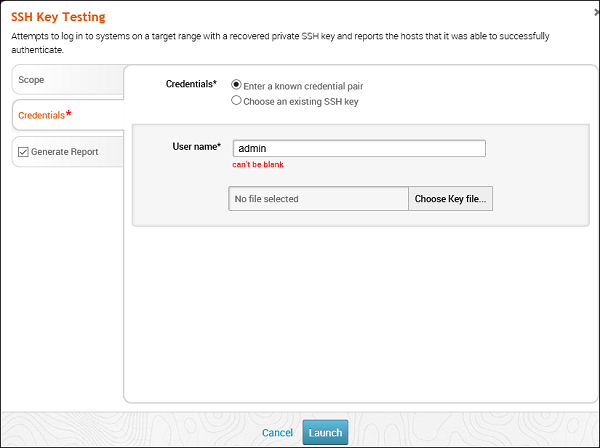
Enter Credentials and click the Launch button.
Passive Network Discovery
This MetaModule is designed to sniff traffic to discover hosts and services on a local network. Since it does not send any packets, you can run this app to conduct a stealthy network discovery scan and identify any hosts, services, and clear-text credentials.
To run this MetaModule, click the Launch button on the opening screen. It will display the following screen.
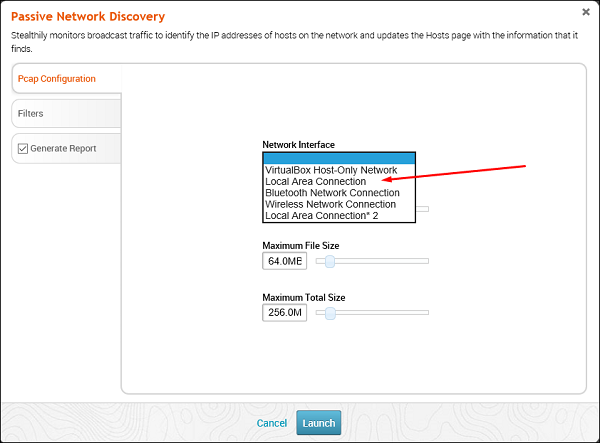
Select the Network interface (Generally they are automatically discovered). Click Filters. Thereafter, check all the protocols that you want to monitor. In this case, we checked only HTTP.
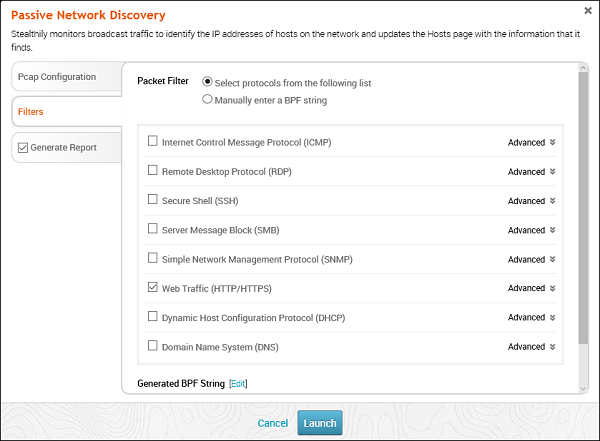
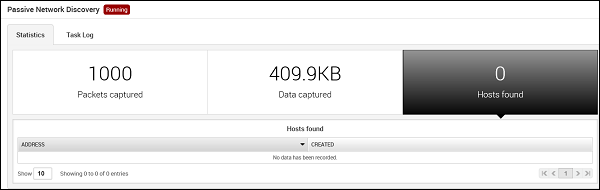
You will get the following screen with captured data and packets. If any IP or credential is found, it will also be displayed.


Post a Comment